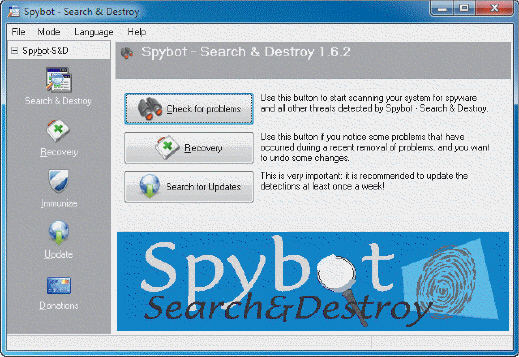
 The application in the accompanying figure is an example of a program that protects against ____.
The application in the accompanying figure is an example of a program that protects against ____.
A. spyware
B. viruses
C. phishing
D. pharming
Answer: A
Computer Science & Information Technology
You might also like to view...
What is OSHA’s mission?
What will be an ideal response?
Computer Science & Information Technology
Show a list of course numbers, their description and their prerequisites. If the prerequisite is null, substitute “None” using NVL and a data conversion function.
What will be an ideal response?
Computer Science & Information Technology
When creating or saving graphics for the Web, you should use the ____ color system.
A. complementary B. secondary C. subtractive D. RGB
Computer Science & Information Technology
The Windows Metafile format is saved with the extension ____.
a. SWF b. WMF c. WIN d. MET
Computer Science & Information Technology