What other ways could Wireshark be used in a production network?
What will be an ideal response?
Wireshark is often used for security purposes for after-the-fact analysis of normal traffic or after
a network attack. New protocols or services may need to be captured to determine what port or
ports are used.
You might also like to view...
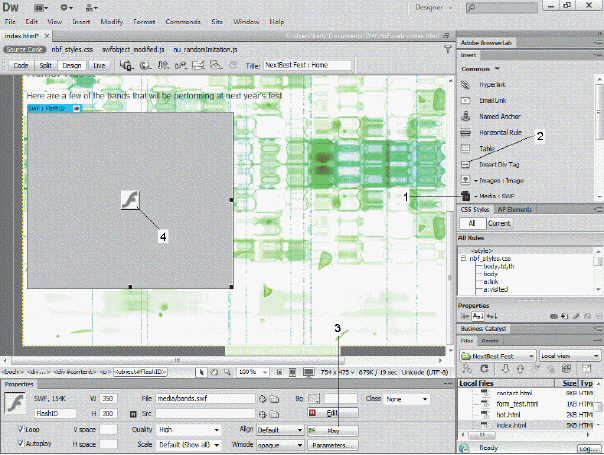 When you save the home page in the accompanying figure, the Copy Dependent Files dialog box opens, stating that the page uses a(n) ____ that requires supporting files that have been copied to the local site.
When you save the home page in the accompanying figure, the Copy Dependent Files dialog box opens, stating that the page uses a(n) ____ that requires supporting files that have been copied to the local site.
A. object B. behavior C. event D. either a or b
The starting address of a structure is the address of the first member of the structure.
Answer the following statement true (T) or false (F)
A(n) ________ is a style type that applies a format to a table and may include specific table elements such as table rows and columns
Fill in the blank(s) with correct word
You must install the Programming tab in order to work with forms, macros, and XML
Indicate whether the statement is true or false