Connecting to a wireless network without the owner's permission is known as ________.
Fill in the blank(s) with the appropriate word(s).
You might also like to view...
What is the purpose of a compiler?
What will be an ideal response?
The data transfer for V.92/90 is called asymmetric operation because the data rate connection to the ISP is at V.24 speeds where the data rate connection from the ISP is at V.92/90 speeds. True or False?
Indicate whether the statement is true or false
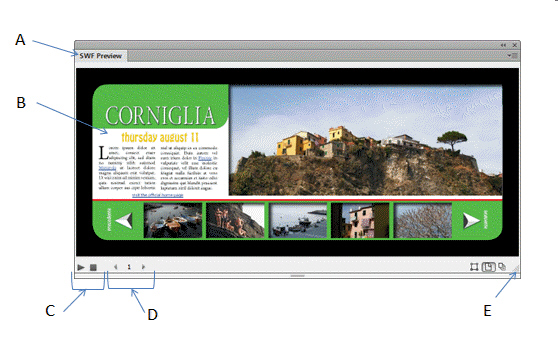 In the accompanying figure, the criterion for Current Due is 0. To find all clients whose current due amount is $2,000.00, erase the 0 in the Current Due column and enter _____ in the Criteria row of the Amount Paid column.
In the accompanying figure, the criterion for Current Due is 0. To find all clients whose current due amount is $2,000.00, erase the 0 in the Current Due column and enter _____ in the Criteria row of the Amount Paid column.
A. =2,000 B. 2,000 C. =$2,000 D. 2000
Which of the following authentication solutions use tickets that include valid credentials to access additional network resources?
A. Kerberos B. RADIUS C. Multi-factor authentication D. TACACS+