?
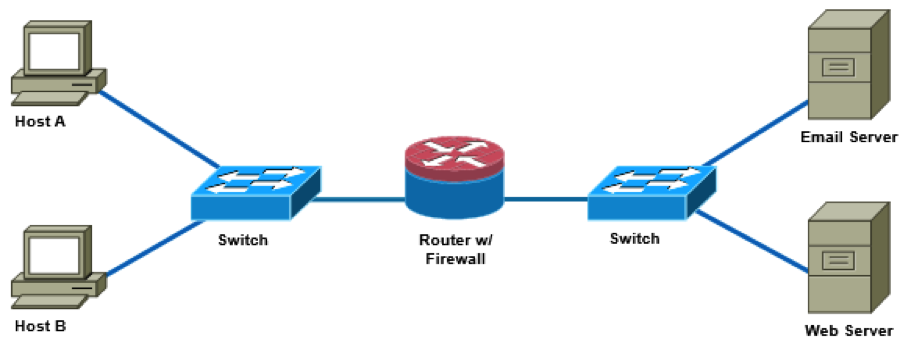
Examine the exhibit above.
Host B is sending an email intended for the user on Host A to the email server. What protocol is being used to send the message through the router?
A. None
B. SMTP
C. POP3
D. SNMP
Answer: B
Computer Science & Information Technology
You might also like to view...
To access the eleventh record in a __________ data file, we must read in the first ten records first.
Fill in the blank(s) with correct word
Computer Science & Information Technology
When a range is selected, the name box displays the cell address of ________
A) all cells in the range B) the first cell in the range C) the last cell in the range D) none of the cells in the range
Computer Science & Information Technology
Which of the following security levels is used for debugging requests, which are generally low priority in terms of security needs?
A) 0 B) 1 C) 6 D) 7
Computer Science & Information Technology
The temptation to add more features and functionality to the original range of the system is called _____.
a. unit testing b. site preparation c. cutover d. scope creep
Computer Science & Information Technology