COGNITIVE ASSESSMENT
Software that sees and possibly records everything that is typed on a keyboard raises the issue of privacy for the person doing the typing. What is this controversial software called?
A. keyfollowing software
B. keyboard monitoring software
C. keycapture software
D. keyhacker software
Answer: B
You might also like to view...
What value would be returned by the function sum for this call?
``` sum ( 67.58, 50.94 ) ``` Definition of sum: ``` int sum( int num1, int num2 ) { return( num1 + num2 ); } ``` a. 118 b. 118.52 c. 119 d. 117
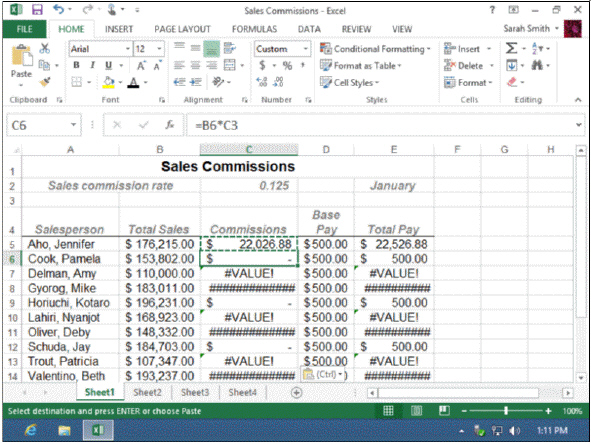 In the accompanying figure, the original formula =B5*C2 works correctly in cell C5. When that formula is copied to cell C7, the relative references in the formula change to _____.
In the accompanying figure, the original formula =B5*C2 works correctly in cell C5. When that formula is copied to cell C7, the relative references in the formula change to _____.
A. =B6*C3 B. =B7*C4 C. =B8*C5 D. =B5*C2
A(n) _______________ shows network devices and how they connect.
Fill in the blank(s) with the appropriate word(s).
Case-based Critical Thinking Questions Case 3-1 Judy wants to be able to validate the XML documents that she uses for recipes. These documents include numeric elements that specify ingredient amounts and cooking times, so you recommend that she use a schema instead of a DTD, and you teach her some of the key facts about schemas. Judy has an element called "recipeName" that she uses to record the name of a recipe. This element only contains text. Which of the following would be a valid XML Schema definition for this element?
A.