Find the distance from 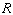 to
to 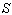 on the graph. Round your answer to the nearest tenth.
on the graph. Round your answer to the nearest tenth. 
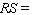 __________ units
__________ units
Fill in the blank(s) with the appropriate word(s).
7.8
You might also like to view...
The ____ tool is used to clone pixels, and allows you to choose its brush size, hardness, and opacity.
A. Cloning B. Draft Clone C. Paint Clone D. Clone Stamp
You can determine if a document is an older Word file or Word 2007 file by looking at its ________
Fill in the blank(s) with correct word
Match each item with a statement below.
A. Responsible for the storage, maintenance, and protection of the information. B. Software programs that reveals its designed behavior only when activated. C. Information remains whole, complete, and uncorrupted. D. Component in a system that allows the attacker to access the system at will, bypassing standard login controls. E. Involves operating an information system that meets the high level of availability sought by system users as well as the confidentiality and integrity needs of system owners and security professionals F. Malicious program that replicates itself constantly. G. Information is free from mistakes or errors. H. Responsible for the security and use of a particular set of information. I. Information is protected from disclosure or exposure to unauthorized individuals or systems.
____ relates to how much one module in a program must rely on another.
A. Coupling B. Cohesion C. Orthogonality D. Reusability