When creating a frequency table using the FREQUENCY function, you must select a range of cells that is one more than the cells containing the bin values
Indicate whether the statement is true or false
TRUE
You might also like to view...
During a bit of careless typing (thinking?) when putting together the ADT for List, the boundary condition for uptoIndex in List.sublist() was given as uptoIndex < size. Below is the specification with the mistake. What are the implications of this? Why is this wrong?
sublist ( int fromIndex, int uptoIndex ) pre-condition: 0 ??fromIndex < size 0 ??uptoIndex < size fromIndex ??uptoIndex responsibilities: provide a sublist (“view”) of this list containing the elements in the positions from fromIndex to uptoIndex – 1 inclusive. The sublist is backed by this list, so changes made to the sublist change this list. Operations on the sublist are undefined if the list is structurally modified in any way except through the sublist post-condition: this list is unchanged throws: index out of bounds exception if pre-conditions are not met returns: a List object containing the elements in the positions fromIndex to uptoIndex – 1, inclusive.
The Shapes button is located in the _____ group on the Insert tab.?
A. ?Images B. ?Illustrations C. ?Apps D. ?Symbols
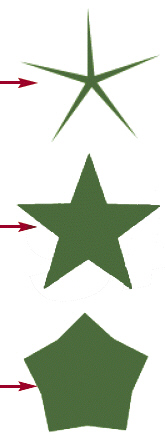 The top star in the accompanying figure has a point size of ____.
The top star in the accompanying figure has a point size of ____.
A. 0 B. 1 C. 5 D. 10
Suppose you want to use an Internet cafe to login to your personal account on a bank web site, but you suspect that the computers in this cafe are infected with software keyloggers. Assuming that you can have both a web browser window and a text editing window open at the same time, describe a scheme that allows you to type in your userID and password so that a keylogger, used in isolation of any
screen captures or mouse event captures, would not be able to discover your userID and password. What will be an ideal response?