____ allow EIGRP to support multiple Network layer routed protocols such as IP, IPX, and AppleTalk.
A. Neighbor discovery and maintenance
B. Protocol Dependent Modules
C. Reliable Transport Protocol
D. Diffusing Update Algorithm (DUAL)
Answer: B
You might also like to view...
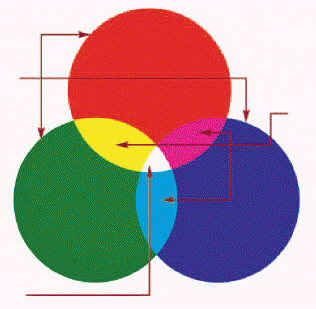 The accompanying figure shows the ____________________ color system.
The accompanying figure shows the ____________________ color system.
Fill in the blank(s) with the appropriate word(s).
?Case 1-3 Damon asks his friend Tanya to test his understanding on computer and business ethics. Tanyaasks Damon to provide a scenario that is an act of plagiarism. Which of the following scenarios can Damon provide?
A. ?A teacher sharing a poem with a class, leading the class to believe the poem was his original work B. ?A newspaper reporter paraphrasing a few sentences or paragraphs written by another author without changing the meaning of the text, including the revised text in an article, and crediting the original author with a proper citation C. ?A student copying and pasting information from various online documents and using those quotes in her research paper either indented or enclosed in quotation marks with the proper citations for each author D. ?A philosopher referring to the information available on the Internet and using certain quotes in her research paper either indented or enclosed in quotation marks with the proper citations for each author
The default importance level for all new messages is ____ importance.
A. low B. high C. normal D. urgent
Stealing hardware, cutting system cable, or taking application software are examples of what type of attack?
A. Worm B. Physical C. Spyware D. Spoofing