In some cases, you might need to change a table's structure in ways that are beyond the capabilities of your DBMS. When that happens, use the RESTRUCTURE command to redesign the table.
Answer the following statement true (T) or false (F)
False
You might also like to view...
The key used in symmetric encryption is referred to as a __________ key.
A. public B. secret C. private D. decryption
Today, ____ remains the LAN protocol of preference for NetWare 6 and above.
A. IPX/SPX B. XNS C. NetBEUI D. TCP/IP
Menus usually use sentinel values to exit.
Answer the following statement true (T) or false (F)
A new Cat6 cable run and keystone jack were installed for a workstation that was moved from the sales department to the shipping department. Since the move, the user has been complaining of slow transfer speeds on both Internet and local network communications. The technician ran a test and is viewing the following output on the tester.
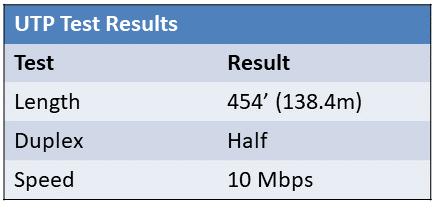
A. The cable run exceeds the specifications for Ethernet over twisted pair. B. The NIC in the workstation is statically set to 10 Mbps/Half-duplex. C. The network switch port is statically set to 10 Mbps/Half-duplex. D. The ISP is experiencing issues with its service to this customer.