What is the prime objective of code signing?
A. To verify the author and integrity of downloadable code that is signed using a public key
B. To verify the author and integrity of downloadable code that is signed using a symmetric key
C. To verify the author and integrity of downloadable code that is signed using a master key
D. To verify the author and integrity of downloadable code that is signed using a private key
Answer: D. To verify the author and integrity of downloadable code that is signed using a private key
You might also like to view...
For the site shown in Figure 8.12 , to embed the image logo.png on the Web page french-roast.html , the document-relative file path is ______.
Fill in the blank(s) with the appropriate word(s).
Discuss the extent to which the RPC style supported by protocol buffers enhances extensibility (especially the design decision to have one argument and one result).
What will be an ideal response?
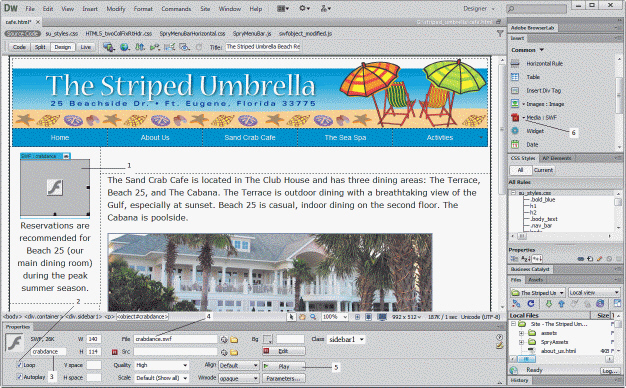 Which item in the accompanying figure refers to the ID text box?
Which item in the accompanying figure refers to the ID text box?
A. 1 B. 3 C. 4 D. 5
Match each type of server to its function:
I. mid-range server II. Web server III. network server IV. file server V. server A. a group of computers run by specialized software B. same functions as a mainframe computer for smaller companies C. computer running specialized software to support Web pages D. organization and managing of files E. powerful, fast computers that run special software for specific purposes