You never want to disable security settings to install software
Indicate whether the statement is true or false
FALSE
You might also like to view...
Crop ________ are used the same way as sizing handles to crop a picture
A) pointers B) handles C) tools D) tabs
FIGURE OL 3-1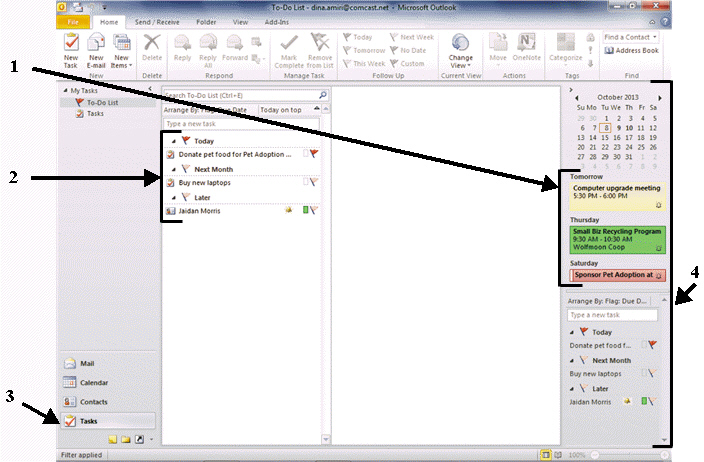 Referring to Figure OL 3-1 above, number 4 is pointing to the ____.
Referring to Figure OL 3-1 above, number 4 is pointing to the ____.
A. To-Do bar B. Task List C. Tasks folder button D. Meetings, appointments, and events
Match the following tools to their uses in the field
I. Log book A. Summarizes the case II. Forensic examiner platform B. Avoid contaminating evidence with your fingerprints III. General case intake form C. Write on CDs without damaging them IV. Gloves D. Use to record investigator actions V. Sharpie E. Use to acquire data in the field
_____ is a systems development technique that tests system concepts and provides an opportunity to examine input, output, and user interfaces before final decisions are made.?
A. ?Scrum B. ?Prototyping C. ?Modeling D. ?Rapid application development