In the ____ phase, the actual database security assessment is conducted.
A. gathering
B. execution
C. mobilizing
D. reconnaissance
Answer: B
You might also like to view...
Robyn Cucurullo is developing a social networking app for tablet computers. She has the following stages completed so far:
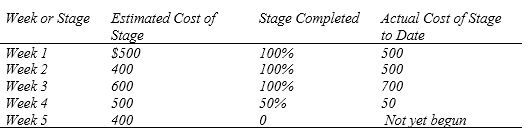
a. Create a table similar to the one in Figure 3.27.
b. For Week 3, calculate the budget at completion (B A C), planned value (P V), actual cost (A C), and earned value (E V) at Week 3.
c. For Week 3, calculate the performance measures of cost variance (C V), schedule variance (S V), the cost performance index (C P I), and the schedule performance index (S P I).
d. What can you tell about the budget in Week 3 by using these performance measures?
e. What can you tell about the schedule in Week 3 by using these performance measures?
f. For Week 3, calculate the estimated time to complete (E T C) and estimate at completion (E A C).
The text-based emoticon :-0 indicates ________
A) anger B) confused C) just kidding D) surprise
Windows and Orphans can be avoided by altering the margins
Indicate whether the statement is true or false
Two or more cells that Excel treats as a single unit is called a:
A) workbook. B) series. C) worksheet. D) range.