The output of this program will be:
Consider the program below:
```
public class Test {
public static void main(String[] args) {
int[] a;
a = new int[10];
for (int i = 0; i < a.length; i++) {
a[i] = i + 2;
}
int result = 0;
for (int i = 0; i < a.length; i++) {
result += a[i];
}
System.out.printf("Result is: %d%n", result);
}
}
```
a. Result is: 62.
b. Result is: 64.
c. Result is: 65.
d. Result is: 67.
c. Result is: 65.
You might also like to view...
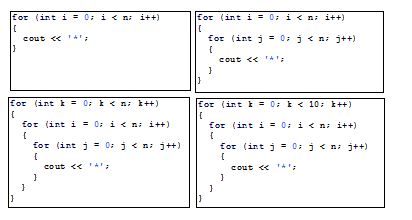
How many stars are displayed in the following code if n is 10? How many if n is 20? Use the Big O notation to estimate the time complexity.
Passing addresses is referred to as a function ____.
a. pass by value b. pass by reference c. call by value d. pass by copy
You are given the task of detecting the occurrences of a polymorphic virus that conceals itself as follows. The body, C, of the virus code is obfuscated by XORing it with a byte sequence, T, derived from a six-byte secret key, K, that changes from instance to instance of the virus in a random way. The sequence T is derived by merely repeating over and over the given key K. The length of the body
of the virus code is a multiple of six—padding is added otherwise. Thus, the obfuscated body is T ? C, where T = K||K|| · · · and || denotes string concatenation. The virus inserts itself to the infected program at an unpredictable location. @par An infected file contains a loader that reads the key K, unhides the body C of the virus code by XORing the obfuscated version with the sequence T (derived from K), and finally launches C. The loader code, key K, and the obfuscated body are inserted at random positions of infected programs. At some point of the execution of the infected program, the loader gets called, which unhides the virus and then executes it. Assume that you have obtained the body C of the virus code and a set of programs that are suspected to be infected. You want to detect the occurrences of this virus among the suspected programs without having to actually emulate the execution of the programs. Give an algorithm to do this in polynomial time in the length of the program. Assume that the loader of the virus is a short piece of code that can be commonly found in legitimate programs. Therefore, it cannot be used as a signature of our virus. Hence, looking for the loader is not an acceptable solution. Remember, the loader is in binary, and as such, extracting information from it is nontrivial, i.e., wrong.
To sort rows in a specific order, use the ____________________ clause with the desired sort key(s).
Fill in the blank(s) with the appropriate word(s).