Security awareness training should be:
a. Mandatory for information workers only
b. Optional
c. Provided at the time of hire and annually thereafter
d. Provided at the time of hire
c. Provided at the time of hire and annually thereafter
You might also like to view...
Case-based Critical Thinking QuestionsCase 13-1Judy wants to be able to validate the XML documents that she uses for recipes. These documents include numeric elements that specify ingredient amounts and cooking times, so you recommend that she use a schema instead of a DTD, and you teach her some of the key facts about schemas. Judy has an attribute called "recipeType" that she uses to record whether the recipe is for an appetizer, entree, dessert, or other type of dish. This attribute only contains text. Which of the following would be a valid XML schema definition for this attribute?
A.
The Transform Again command does not work with the ____ command.
A. Copy B. Offset Path C. Rotate D. Move
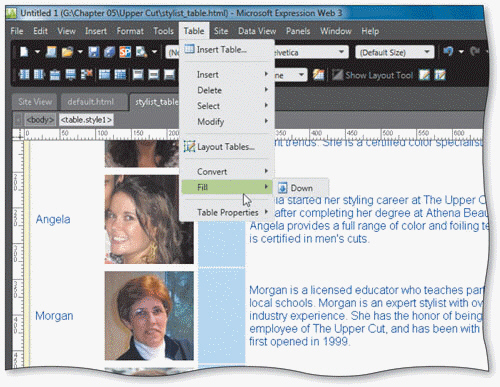 Using the accompanying figure as your guide, list the steps to fill a range of cells in the same column with existing content.
Using the accompanying figure as your guide, list the steps to fill a range of cells in the same column with existing content.
What will be an ideal response?
You can return an array from a function.
Answer the following statement true (T) or false (F)