In IPsec, authentication is accomplished by the ____ protocol.
A. Encapsulating Security Payload (ESP)
B. ISAKMP/Oakley
C. Authentication Header (AH)
D. L2TP
Answer: C
You might also like to view...
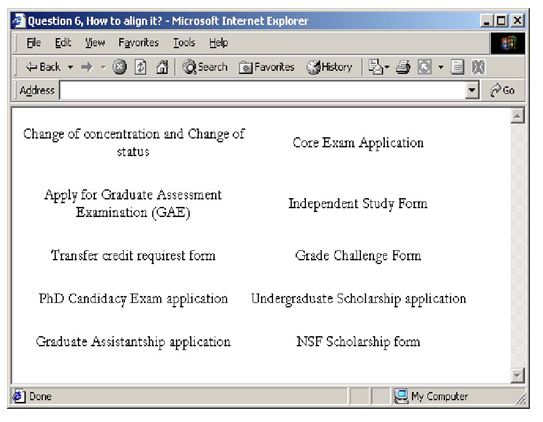
Figure 5-21 is an example that’s not well aligned. Explain what you would do to improve the alignment. It may be helpful to create a photocopy of the example and draw on it.
Google+ is an example of a(n) ________ network
Fill in the blank(s) with correct word
Which of the following is not a selection of options related to downloading and installing updates?
a. Install updates automatically (recommended) b. Download updates but let me choose whether to install them c. Email me when updates are available d. Never check for updates (not recommended)
Answer the following statements true (T) or false (F)
1. A nested decision structure can be used to test more than one condition. 2. A nested decision structure can achieve the same logic as a case structure. 3. The first line of a case structure starts with the word CASE, followed by the test expression. 4. A decision structure will produce unpredictable results if the programmer does not use proper indentation in the pseudocode. 5. An If-Then-Else statement must be used to write a single alternative decision structure.