A(n) ____________________ model excludes users from access to resources, by default, and then adds whatever users need access to such resources as exceptions to the general exclusionary rule.
Fill in the blank(s) with the appropriate word(s).
pessimistic security
Computer Science & Information Technology
You might also like to view...
The method printf is used only to format the output of integers and decimal numbers.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
At most how many keys can be inserted in the children of the leftmost node (with the separator key e) in the middle level without splitting that node?
Consider the following B+ tree:
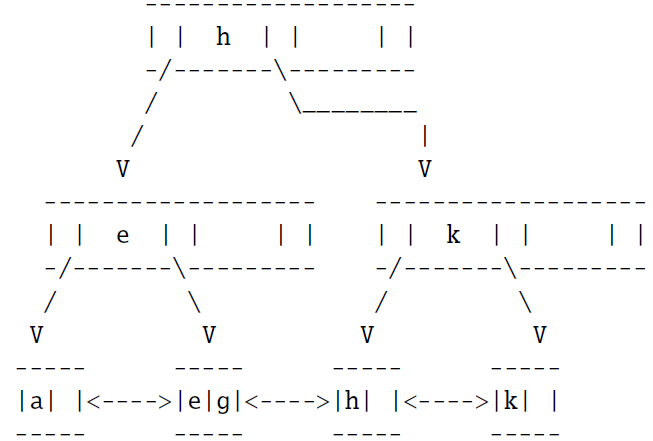
Computer Science & Information Technology
____________________ an area keeps it safe from any digital paint you apply.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Explain how the police use computers as a crime-fighting aid.
What will be an ideal response?
Computer Science & Information Technology