In computer security, a threat ____ is an attempt (usually in the form of a document or diagram) to systematically identify the ways that technology might be vulnerable to a malicious attack.
A. simulation
B. analysis
C. construction
D. encapsulation
Answer: B
Computer Science & Information Technology
You might also like to view...
Define boxing and unboxing.
What will be an ideal response?
Computer Science & Information Technology
Which of the following is not an advantage of using a logical model?
A) A system based on a logical model is more stable. B) The logical model helps the analyst understand the business being studied. C) It facilitates communication with the users. D) A logical model clarifies which processes are automated.
Computer Science & Information Technology
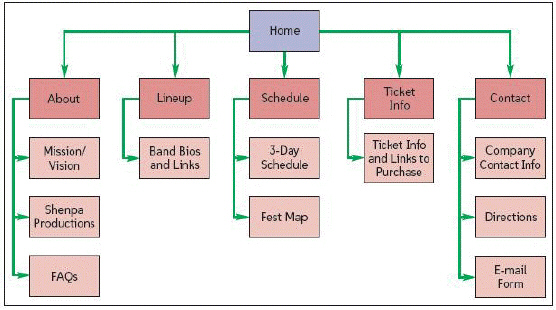 In Web design, the lines of the item in the accompanying figure represent ____.
In Web design, the lines of the item in the accompanying figure represent ____.
A. Web pages B. the connection of Web pages C. decision points D. steps
Computer Science & Information Technology
Press ________ to start a presentation from the first slide
A) F4 B) F9 C) F5 D) F1
Computer Science & Information Technology