The operating system performs all of the following tasks except
A. translates third-generation languages into machine language
B. assigns memory to applications
C. authorizes user access
D. schedules job processing
Answer: C
You might also like to view...
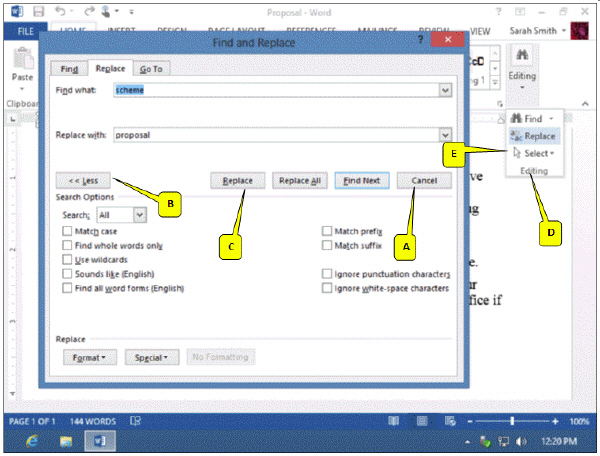 Refering to the accompanying figure, which of the following search options should be selected if you are looking for a word but are not sure how to spell it?
Refering to the accompanying figure, which of the following search options should be selected if you are looking for a word but are not sure how to spell it?
A. Match case B. Find whole words only C. Sounds like D. Nothing
A technician disassembles a desktop computer. After completely reassembling the unit, the technician observes that the motherboard standoffs were not installed. Read each statement below and select the one that best explains how the technician should handle the situation
A) There is always a screw or washer left over. These things actually don't make a difference in the performance of the computer. B) Start up the computer and take no other action if it works. C) Correctly install the standoffs to prevent grounding problems or worse. D) Push the standoffs against the traces until the traces touch the metal case and tape the standoffs in place. Boot the computer and complete the system check-up.
A security analyst is reviewing a web application. If an unauthenticated user tries to access a page in the application, the user is redirected to the login page. After successful authentication, the user is then redirected back to the original page. Some users have reported receiving phishing emails with a link that takes them to the application login page but then redirects to a fake login page after successful authentication. Which of the following will remediate this software vulnerability?
A. Enforce unique session IDs for the application. B. Deploy a WAF in front of the web application. C. Check for and enforce the proper domain for the redirect. D. Use a parameterized query to check the credentials. E. Implement email filtering with anti-phishing protection.
The advantages of using a ____ are that you can have an object move along any path, including a path that intersects itself, and you can easily change the shape of the path, allowing you to experiment with different motions.
A. motion guide B. keyframe C. bitmap D. playhead