The process of calling a module requires several actions to be performed by the computer. This is referred to as __________.
a. overhead
b. maintenance
c. memory
d. efficiency
a. overhead
You might also like to view...
When a layer is ____ as shown in the accompanying figure, you can see through it to the layers below.
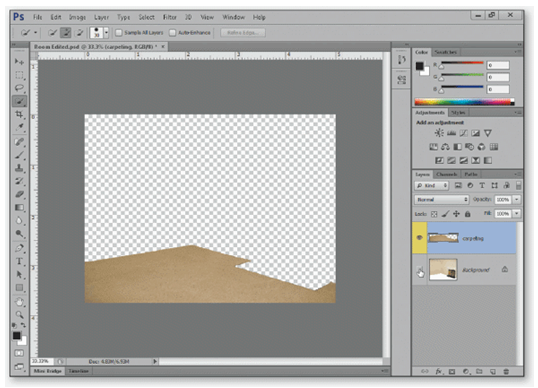
a. transparent
b. nontransparent
c. opaque
d. resampled
What is the best way to restrict URL access?
A. Redirect visitors to another page. B. Make sure sensitive pages require authentication. C. Use the"secure"flag on all sensitive cookies. D. Use Secure Shell (SSH).
Firefox does not stop the spinning icon in the browser's upper-right corner that indicates a document is loading until the close() method executes.
Answer the following statement true (T) or false (F)
The Remove tab feature removes both opening and closing tabs while leaving the content between the tags intact.
Answer the following statement true (T) or false (F)