Match the following macro actions to their description
I. AutoExec
II. ApplyFilter
III. DisplayHourglassPointer
IV. GoToControl
V. Beep
A. Restrict or sort records
B. Moves the focus
C. Uses the computer's speakers
D. Runs when the database is opened
E. Provides a visual indication
D, A, E, B, C
You might also like to view...
The relation shown in Figure 15.11 lists members of staff (staffName) working in a given ward (wardName) and patients (patientName) allocated to a given ward. There is no relationship between members of staff and patients in each ward. In this example assume that staff name (staffName) uniquely identifies each member of staff and that the patient name (patientName) uniquely identifies each patient.
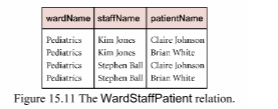
(a) Describe why the relation shown in Figure 15.11 is in BCNF and not in 4NF.
(b) The relation shown in Figure 15.11 is susceptible to update anomalies. Provide
examples of insertion, deletion, and update anomalies.
(c) Describe and illustrate the process of normalizing the relation shown in Figure 15.11 to 4NF.
Write the statement to do the following:- create a two-dimensional array called orders- each element will be of the int data type- there will be 2 rows and 3 columns- each element will be initialized to 0
What will be an ideal response?
To preserve the confidentiality and integrity of the database requires:
A. biometric devices B. user-defined procedures. C. backup controls D. inference controls .
A data file is one that _____.
A. a user can work with or manipulate B. instructs a computer to perform a task C. is not saved to a specific location D. contains a program or an app