________ is the standard internal drive interface used to connect drives to the motherboard
Fill in the blank(s) with correct word
SATA, Serial ATA
You might also like to view...
Critical Thinking QuestionsCase 2-1Tom is a golf pro, and he is using Outlook to manage his schedule. Some of his customers pay him for a single lesson, while others set up regular weekly lessons. In addition, Tom is coordinating the annual two-day tournament at his local golf course.According to the way that Outlook defines calendar items, what type of item is a regular weekly lesson, if you assume that the person taking the lesson is NOT invited to the lesson using Outlook? a. recurring appointmentc. recurring eventb. recurring meetingd. one-time appointment
What will be an ideal response?
Write an application that encrypts a message from the user (Fig. 23.18). The application should be able to encrypt the message in two different ways: substitution cipher and transposition cipher (both described below). The user should be able to enter the message in a JTextField and select the desired method of encryption. The encrypted message is then displayed in an uneditable JTextField. In a substitution cipher, every character in the English alphabet is represented by a dif- ferent character in a substitution String, which we will refer to as the substitution alphabet. Every time a letter occurs in the English sentence, it is replaced by the letter in the corre- sponding index of the substitution String. As an example of a substitution cipher, let’s e
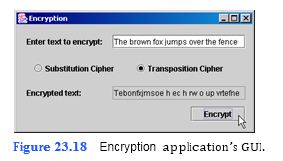
a) Copying the template to your working directory. Copy the C:Examples Tutorial23ExercisesCipherEncryption directory to your C:SimplyJava directory.
b) Opening the template file. Open the Encryption.java file in your text editor.
c) Adding code to the substitutionCipher method. In the substitutionCipher method (lines 126–140), English and substitution alphabet Strings have been declared for you as normalAlphabet and cipherAlphabet, respectively. Other Strings that you will be using have already been defined for you—cipher is an empty String you will use to store the encrypted text and plain contains the text entered by the user. After the declaration of the Strings, add an empty for state- ment that loops for each character in plain.
d) Performing the substitution encryption. Inside the for statement you added in Step c, create an int variable index and assign to it the index in normalAlphabet where the current character in plain
Identify the letter of the choice that best matches the phrase or definition.
A. The number of values in an array sized this way is determined at execution B. The index used to refer to a value in the first element within an array C. This method requires that the array is already sorted to produce correct results D. An array with this kind of index declared is not implicitly sized E. Type of arrays that store related data in two or more arrays F. An array can be returned as a result from this G. Arrays that store the elements of tables H. When this procedure is applied to an array, the lowest value is placed in the first element I. An individual item in an array J. Kind of variable that can store more than one value
To show the details of groups in a PivotTable report that are not currently showing, ________ the groups
A) lengthen B) expand C) filter D) show