What is the purpose/function of the following commands?
1. R1(config)# access-list 10 permit host 10.10.20.250
2. R1(config)# access-list 100 deny tcp 172.50.12.0 0.0.0.255 172.50.10.0 0.0.0.255 eq 23
3. R1(config)# access-list 100 permit ip any any
4. R1(config-if)# ip access-group 100 in
5. R1(config)# access-list 101 permit tcp 0.0.0.0 255.255.255.255 130.120.110.100 0.0.0.0 eq 80
6. R1(config)# access-list 101 deny ip any any
7. R1(config-if)# no ip access-group 100 in
8. R1(config)# access-list 122 permit udp any eq domain host 192.168.1.1 gt 1023
9. R1(config)# access-list rate-limit 10 mask 07
1. This access list permits data traffic from 10.10.20.250. The host command indicates a wildcard
mask of 0.0.0.0.
2. This access list denies Telnet packets (port 23) from 172.50.12.0 going to 172.50.10.0.
3. This access list is typically placed at the end of the access list to permit IP traffic from going anywhere. This is added because there is an implicit deny with the access-list.
4. This applies access list 100 on the inbound direction.
5. This permits any TCP data (web traffic) going to the specific IP address 10.120.110.110.
6. This statement denies any source to any destination.
7. Turns off access list 100 on the inbound direction.
8. This access list permits Domain Name System (DNS) access through your firewall to the DNS
server 192.168.1.1.
9.
```
This assigns packets with an IP Precedence of 0, 1, or 2 to the rate-limit access list 10.
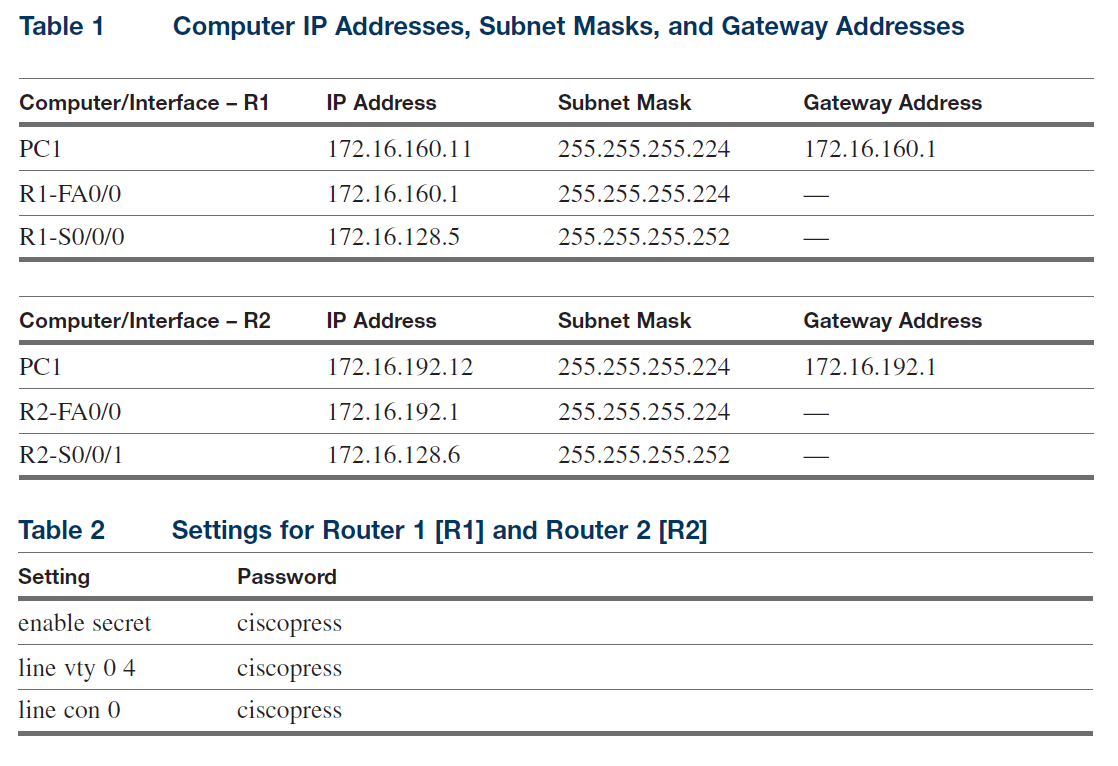
R1
R1# sh running-config
Building configuration...
Current configuration : 800 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$KXED$S08d0zG3x3aiaeFjy7nCP
!
no aaa new-model
!
resource policy
!
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 172.16.160.1 255.255.255.224
!
interface FastEthernet0/1
no ip address
shutdown
!
interface Serial0/0/0
ip address 172.16.128.5 255.255.255.252
ip access-group 100 in
clock rate 128000
!
interface Serial0/0/1
no ip address
shutdown
!
log-adjacency-changes
router rip
no auto-summary
version 2
network 172.16.0.0
!
!
!
ip http server
no ip http secure-server
!
!
!
access-list 100 deny udp any any
access-list 100 permit ip any any
access-list 100 deny tcp any any eq telnet
access-list 100 permit ip any any
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
!
line con 0
password ciscopress
login
line aux 0
login local ciscopress
line vty 0 4
password ciscopress
login
!
scheduler allocate 20000 1000
!
end
R1#
R2
R2# sh running-config
Building configuration...
Current configuration : 800 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$KXED$S08d0zG3x3aiaeFjy7nCP
!
no aaa new-model
!
resource policy
!
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 172.16.192.1 255.255.255.224
ip access-group 100 in
!
interface FastEthernet0/1
no ip address
shutdown
!
interface Serial0/0/0
no ip address
shutdown
!
interface Serial0/0/1
ip address 172.16.128.6 255.255.255.252
!
log-adjacency-changes
router rip
no auto-summary
version 2
network 172.16.0.0
!
!
!
ip http server
no ip http secure-server
!
!
!
access-list 100 deny tcp 172.16.192.0 0.0.0.255 172.16.160.0 0.0.0.255 eq telnet
access-list 100 permit ip 172.16.128.0 0.0.0.255 172.16.160.0 0.0.0.255
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
!
line con 0
password ciscopress
login
line aux 0
login local ciscopress
line vty 0 4
password ciscopress
login
!
scheduler allocate 20000 1000
!
end
R2#
```
You might also like to view...
What would be the value of numS if the following pseudocode was coded and run?
``` Declare String prose = "she sells seashells at the seashore" Declare Integer counter Declare Integer numS = 0 For counter = 0 to length(prose) If substring(prose, counter, counter) == "s" Then Set numS = numS + 1 End If End For ``` a. 6 b. 8 c. 30 d. 35
The ________ View offers more flexibility in generating queries
Fill in the blank(s) with correct word
Celina, a Human Resource (HR) manager, creates a graph on an Excel sheet representing the attrition rate in the past five years in her company. She presents the graph such that the graph area occupies the entire worksheet without any worksheet cells. In this case, Celina presents a _____.?
A. ?spreadsheet B. ?sparkline C. ?chart sheet D. ?pivot table
Julio needs to write a report and develop a budget for his job. what type of apps should he use to complete these tasks?