84.The TCP/IP model is a(n) __________ layer model.
Fill in the blank(s) with the appropriate word(s).
four (4)
correct
You might also like to view...
A String constructor cannot be passed ________.
a. char arrays. b. int arrays. c. byte arrays. d. Strings.
The Windows 8 utility that provides disk imaging is called _____.
A. Backup and Restore B. File History C. Windows 7 File Recovery D. Disk Recovery
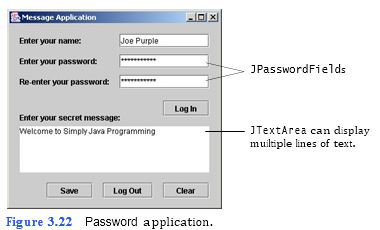
Password GUI) In this exercise, you apply the GUI design guidelines you have learned to a graphical user interface for a password-protected message application (Fig. 3.22). You will set the bounds of the Enter your secret message: JTextArea such that it is left aligned with the Enter your secret message: JLabel and right aligned with the Log In JButton.
a) Copying the template to your working directory. Copy the C:ExamplesTutorial03ExercisesPassword directory to your C:SimplyJava directory.
b) Opening the Command Prompt window and changing directories. Open the Command Prompt by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJavaPassword, then pressing Enter.
c) Compiling the template application. Compile your application by typing javac Password.java, then pressing Enter.
d) Running the template application. Run the application by typing java Password.
The GUI of the Password template application should appear as shown in Fig. 3.23. Notice the differences from Fig. 3.22.
e) Closing the application. Close your running application by clicking its close button. f) Opening the template file. Open the Password.java file in your text editor.
g) Customizing the Enter your secret message: JTextArea. Using Fig. 3.22 and the template code as a guide, you wi
boolean found = false;int num;int square;while (!found){ num = console.nextInt(); square = num * num; if (square > 40) found = true;}The above code is an example of a(n) ____ loop.
A. flag-controlled B. counter-controlled C. EOF-controlled D. sentinel-controlled