Security threats can originate from ________.
a) malicious users
b) malicious software
c) outside the system via a network connection
d) all of the above
d) all of the above
You might also like to view...
What would happen if the try statement were removed from the level1 method of the ExceptionScope class in the Propagation program?
What will be an ideal response?
When working with charts, chart data can only be displayed when you are using Layout view
Indicate whether the statement is true or false
The table lists some braking distances based on the speed of the car when the brakes are applied. The formula for calculating the braking distance needed when traveling at a certain speed is 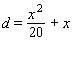 where
where ![]() is the speed of the car and d is the stopping distance. Calculate the stopping distance required when a car is traveling
is the speed of the car and d is the stopping distance. Calculate the stopping distance required when a car is traveling ![]() mph. Use this result and the results in the table to graph this function in mph
mph. Use this result and the results in the table to graph this function in mph
and ft.
Speed of Car (mph)4550556065Stopping Distance (ft)146175206240276
A. 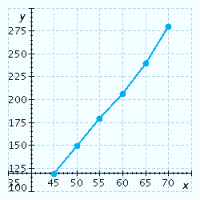
B. 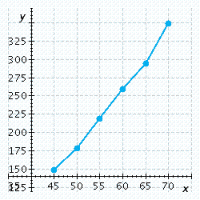
C. 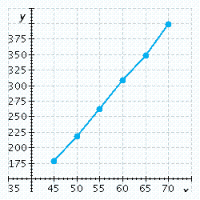
D. 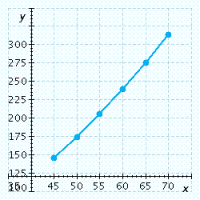
E. 
Always use the ____________________ command after importing a Word file.
Fill in the blank(s) with the appropriate word(s).