The header of a two-page letter includes the ____.
A. recipient's full name, Page 2, and the date
B. recipient's full name, the date, and Page 2
C. the sender's full name, Page 2, and the date
D. the sender's full name, the date, and Page 2
Answer: A
You might also like to view...
A derived class has access to
a. the private functions and variables of its ancestor classes b. the public functions and variables of its ancestor classes c. only the functions and variables defined it its class d. none of the above
________ intrusion-detection software monitors traffic on a network for any unusual patterns that might indicate DoS attacks or attempted entry into a network by an unauthorized user.
a) Host-based. b) Firewall-based. c) Network-based. d) None of the above
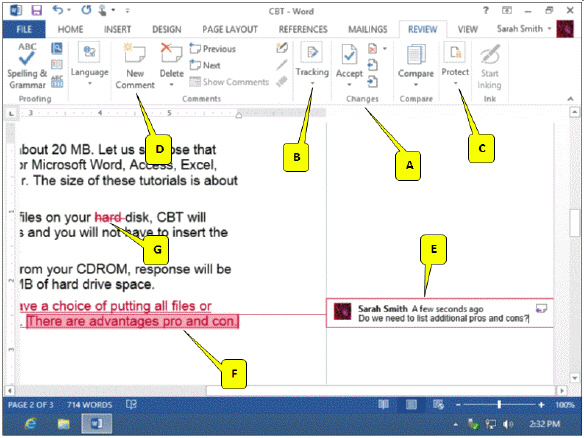 Refering to the accompanying figure, which of the following callouts points to the group of tools used to accept or reject changes?
Refering to the accompanying figure, which of the following callouts points to the group of tools used to accept or reject changes?
A. A B. B C. C D. D
A server process maintains a shared information object such as the BLOB object of Exercise 1.7. Give arguments for and against allowing the client requests to be executed concurrently by the server. In the case that they are executed concurrently, give an example of possible ‘interference’ that can occur between the operations of different clients. Suggest how such interference may be prevented.
What will be an ideal response?