In Figure16.10, if connect fails, can sockfd be reused if we call getsockopt(2) with the SO_ERROR socket option to clear the socket error? Try it and describe what happens
What will be an ideal response?
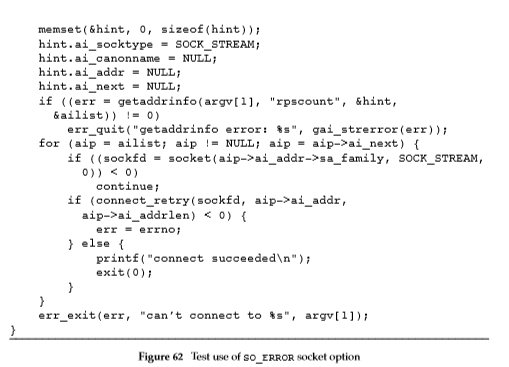
he program shown in Figure 62 uses a modi?ed version of Figure16.10 to reuse the same socket descriptor when a connect request fails. To test it, we run the program on a client system, but without a server process running on the server system. This causes the ?rst connect request to fail with errno set to ECONNREFUSED.While the client is sleeping after the ?rst failure, we can start the server from Exercise 16.4. If the call to getsockopt is able to clear the error on the client socket, the next call to connect should succeed. This behaves as we expect when the client system is Linux 3.2.0 or Solaris 10. However,when the client system is FreeBSD 8.0 or Mac OS X 10.6.8, successive calls toconnectfail witherrnoset toEINVAL. Unfortunately,that the test works on Linux 3.2.0 and Solaris 10 is morebecause these implementations don’t render a socket descriptor unusable when it encounters an error than because they support the SO_ERROR socket option. Comment out the call togetsockoptand verify this behavior
You might also like to view...
What are swap partitions and how are they used?
What will be an ideal response?
The most commonly used accounting software in business is an office application suite, such as Microsoft Office
Indicate whether the statement is true or false
____ references are seldom used other than when creating tables of calculated values such as a multiplication table in which the values of the formula or function can be found in the initial rows and columns of the table.
A. Absolute B. Relative C. Mixed D. Matched
The solution to the problem of ensuring that a person who sent something is the person you believed them to be is some form of _______________.
Fill in the blank(s) with the appropriate word(s).