A __________ activates a function
Fill in the blank(s) with the appropriate word(s).
function call
Computer Science & Information Technology
You might also like to view...
List four of the common work functions specified in the EBK for the management of network and telecommunications security.
What will be an ideal response?
Computer Science & Information Technology
What can you do to reduce the use of virtual memory?
What will be an ideal response?
Computer Science & Information Technology
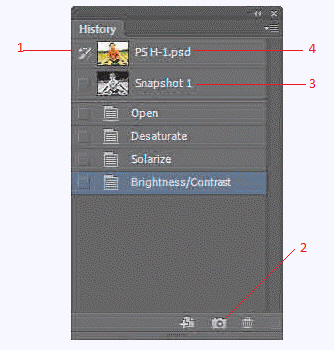 In the accompanying figure, which number represents the Create new snapshot button?
In the accompanying figure, which number represents the Create new snapshot button?
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
Pathnames in a hierarchical file system can become lengthy.Given that the vast majority of file references are made to a user’s own files, what convention might the file system support to minimize the need for using lengthy Pathnames
What will be an ideal response?
Computer Science & Information Technology