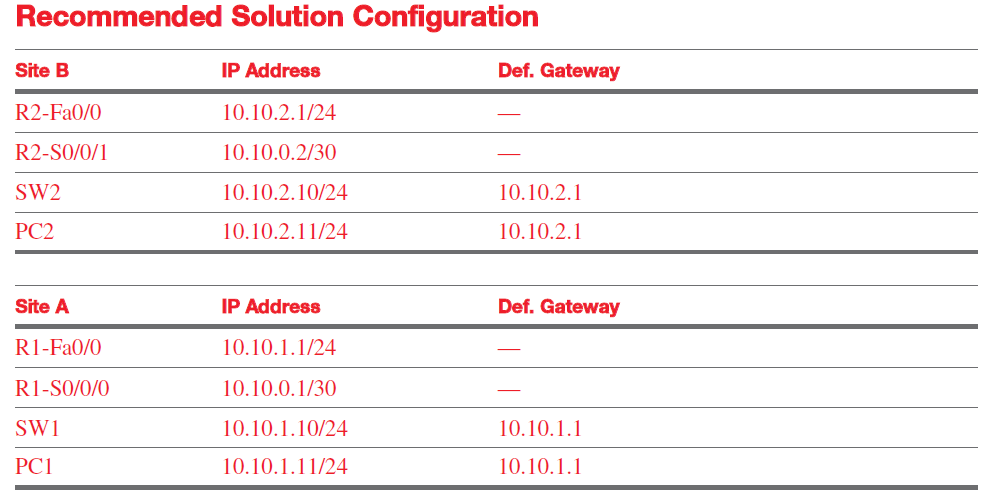
Configure the network according to the specifications listed. Make sure that you address both the router and switch access rules. Test your network carefully, and then save your configuration. You will be asked to demonstrate your network to your instructor.
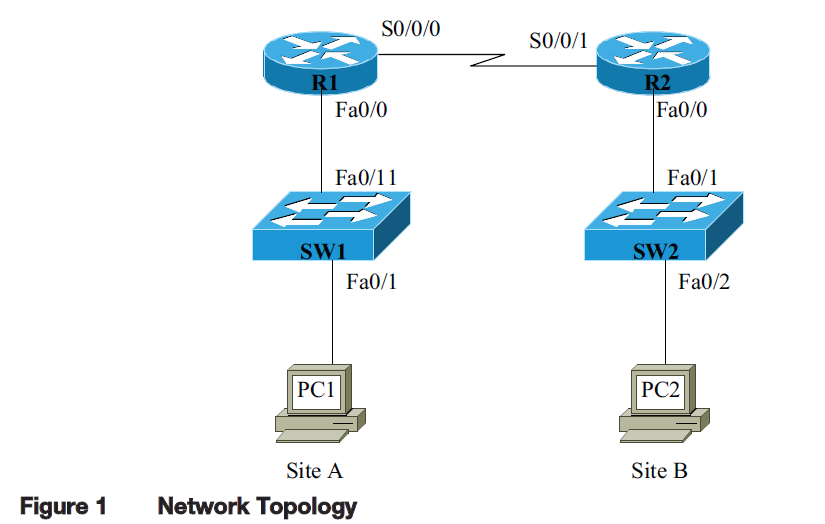
In this exercise, you are to configure NAT (Network Address Translation) for both networks (Site A
and Site B). The network topology for this network is provided in Figure 1. You are to use your
own IP addressing scheme.
Specifics
Router access rules:
? Only computers in Site A are allowed to configure R1.
? Only computers in Site B are allowed to configure R2.
? Access to routers is restricted to the use of the console port and Secure Shell (SSH) connection
(use Telnet if SSH is unavailable).
? All unused ports should be shut down.
? NAT must be used to map all private IPs to one public IP.
Switch access rules:
? Only computers in Site A are allowed to configure SW1.
? Only computers in Site B are allowed to configure SW2.
? Access to switches is restricted to the use of the console port and SSH connection (use Telnet if
SSH is unavailable).
```
R1
R1(config)# ip nat inside source list 20 interface serial 0/0/0 overload
R1(config)# access-list 20 permit 10.10.1.0 0.0.0.255
R1(config)# ip domain-name ciscopress.com
R1(config)# username Cisco password ciscopress
R1(config)# line con 0
R1(config-line)# login local
R1(config-line)# line vty 0 4
R1(config-line)# access-class 20 in
R1(config-line)# transport input ssh telnet
R1(config-line)# login local
R2
R2(config)# ip nat inside source list 20 interface serial 0/0/1 overload
R2(config)# access-list 20 permit 10.10.2.0 0.0.0.255
R2(config)# ip domain-name ciscopress.com
R2(config)# username Cisco password ciscopress
R2(config)# line con 0
R2(config-line)# login local
R2(config-line)# line vty 0 4
R2(config-line)# access-class 20 in
R2(config-line)# transport input ssh telnet
R2(config-line)# login local
SW1
SW1(config)# access-lis
You might also like to view...
When working with pathnames in Linux, the ____________________ path method states the full pathname starting from the root (/).
Fill in the blank(s) with the appropriate word(s).
To have a global positioning system that works in three dimensions from anywhere in the world, a minimum of 24 satellites, orbiting the earth in 6 different orbits, are needed
Indicate whether the statement is true or false
The ________ object allows Access actions to be performed from within VBA
A) DoCmd B) VbaCmd C) RunCmd D) GoCmd
Answer the following statement(s) true (T) or false (F)
1. An Exposure box on the Dodge/Burn options bar allows you to specify a percentage of dodging or burning. 2. You can use the Lens Correction filter to rotate an image or fix image perspective caused by vertical or horizontal camera tilt. 3. Angle error is a lens defect that causes straight lines to bow out toward the edges of the image. 4. Chromatic aberration appears as a color fringe along the edges of objects caused by the lens focusing on different colors of light. 5. Keystone distortion is a lens defect that causes straight lines to bend inward.