Permanently making data inaccessible according to Department of Defense standards can be done with which of the following techniques?
a. Using Windows Delete utility, followed by emptying the Recycle Bin.
b. The EraseAll utility in Windows performs a DoD compliate file deletion.
c. Using a wiping utility that overwrites the medium surface multiple times with random zeroes and ones.
d. Incinerating the medium.
c. d.
You might also like to view...
Red, green, and blue are the ____________________ primary colors of light.
Fill in the blank(s) with the appropriate word(s).
An alternative to embedding audio into a presentation is to ________ the file
Fill in the blank(s) with correct word
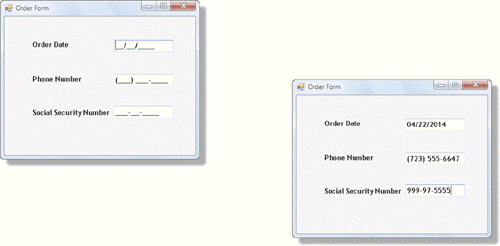 As shown in the accompanying figure, a(n) ____________________ object allows you to specify the data format of the value typed into the text box.
As shown in the accompanying figure, a(n) ____________________ object allows you to specify the data format of the value typed into the text box.
Fill in the blank(s) with the appropriate word(s).
The act of working toward a common business goal with other employees is _______
Fill in the blank(s) with correct word