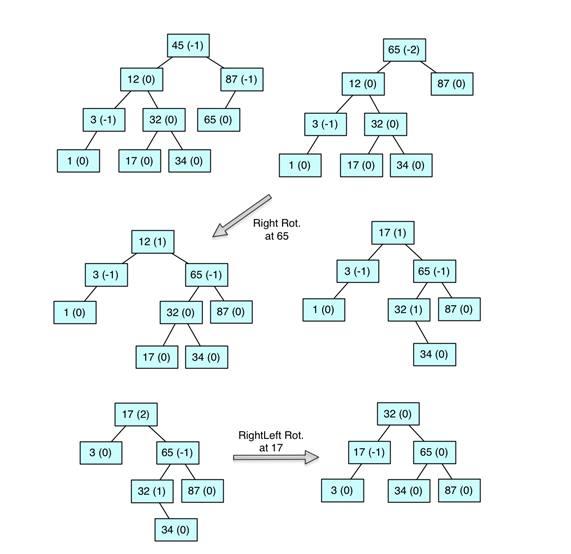
this time assuming an AVL tree and using the result of Exercise 20.3 as a starting point. Include the balance factors in your drawing.
What will be an ideal response?
You might also like to view...
Which of the following statements regarding the rules of search and seizure is NOT true?
A. Seizure of evidence can only occur if the evidence is specifically listed as part of the search warrant unless the evidence is in plain view. B. Evidence specifically listed in the search warrant can be seized. C. Search and seizure rules apply to private organizations and individuals. D. The search can only occur in areas specifically listed in the warrant.
Executable profiling and threshold monitoring are examples of which of the following?
a. Preemptive blocking b. Infiltration c. Anomaly detection d. Sniffing
The Spanning Tree Protocol stipulates that on any bridge, only one root port, which is the bridge's port that is closest to the root bridge, can forward frames toward the root bridge.?
Answer the following statement true (T) or false (F)
Which statement is true?
a) Programs should be written as collections of small functions. b) A function must be no longer than one page. c) The best engineered functions have many parameters and perform many distinct tasks. d) Every function must include an explicit return statement.