________ enables you to track actions performed by users across the domain, such as logging on and off or file and folder access
a. Roaming
b. Logging
c. Publishing
d. Auditing
D. When you create and apply an auditing policy, auditable events are recorded in the security log of the computer at which they happen.
You might also like to view...
A(n) ________ graphic is a designer-quality visual representation of your information
Fill in the blank(s) with correct word
Members of the LinkedIn site may receive requests from other contacts regarding employment or consulting opportunities or inquiries related to their jobs or expertise.
Answer the following statement true (T) or false (F)
The Device Manager allows you to ??display a list of _____ devices installed on your computer.
Fill in the blank(s) with the appropriate word(s).
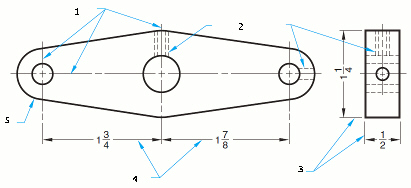 Files containing ____, like those in the accompanying figure, are available from a variety of sources.
Files containing ____, like those in the accompanying figure, are available from a variety of sources.
A. task panes B. search terms C. colors D. graphics