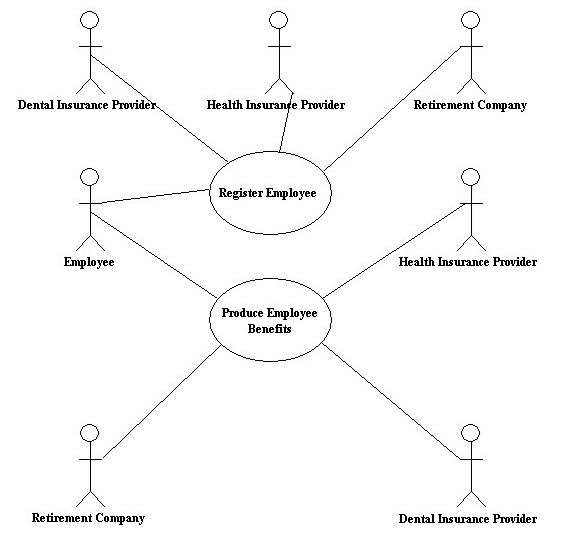
Carson, who is a member of the human resources department at the Elrod Manufacturing Company plant is constantly being asked by employees how much is taken out of their paychecks for insurance, taxes, medical, mandatory retirement, and voluntary retirement. “It takes up to a few hours every day,” says Carson.
He would like a Web system that would allow employees to use a secure logon to view the information. Carson wants the system to interface with health and dental insurance companies to obtain the amount remaining in the employee’s account for the year. He would also like to obtain retirement amounts saved along with investment results. Carson has a high regard for privacy and wants the system to have employees register and give permission to obtain financial amounts from the dental insurance and retirement companies. Draw a use case diagram representing the activities of the employee benefit system.
You might also like to view...
 In the accompanying figure, the item labeled ____ is the protocol.
In the accompanying figure, the item labeled ____ is the protocol.
A. 1 B. 2 C. 3 D. none of the above
A data source that is created in Word is saved as a(n) ________ file type
Fill in the blank(s) with correct word
Social engineering includes viruses, worms, and Trojan horses
Indicate whether the statement is true or false
How is a posture assessment performed on an organization?
a. A thorough examination of each aspect of the organization's network is performed to determine how it might be compromised. b. A third party organization is tasked with attempting to break into the organization and compromise security in order to determine threat vectors. c. A report of data that is subject to special regulation is created, such that the organization is aware of what data needs protection. d. An assessment of how a network will perform under stress is performed to determine if the network throughput is adequate.