What should you implement to prevent man-in-the-middle attacks against the Diffie-Hellman algorithm?
A. One-way hash
B. Digital certificates
C. Zero Knowledge Proof
D. Private keys
B You should implement digital certificates to prevent man-in-the-middle attacks against the Diffie-Hellman algorithm.
You might also like to view...
Discuss some of the primary or more common constraints with project resources.
What will be an ideal response?
Match each of the following terms to its meaning:
I. run II. sketch III. library IV. IDE V. interact A. The output of Processing language B. programming environment C. execute the program D. collections of additional functionalities E. control the sketch with human input
In the accompanying figure that shows the header and footer in a Microsoft Word 2016 document, Box A points to the _____.?
?
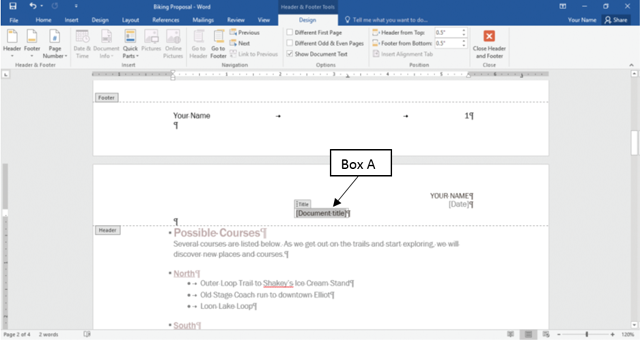
A. ?title reference marker B. ?title template C. ?title citation D. ?title content control
In C++, >> is used as a stream extraction operator and as a right shift operator.
Answer the following statement true (T) or false (F)