Which of the following is not a valid use for key risk indicators?
A. Provide warnings before issues occur.
B. Provide real-time incident response information.
C. Provide historical views of past risks.
D. Provide insight into risk tolerance for the organization.
Answer: B. Provide real-time incident response information.
You might also like to view...
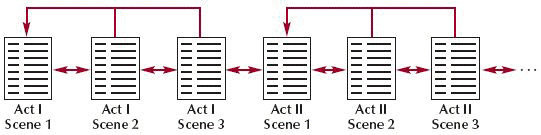 The structure shown in the accompanying figure is an augmented linear structure.
The structure shown in the accompanying figure is an augmented linear structure.
Answer the following statement true (T) or false (F)
The icon labeled 7 in the accompanying figure represents the ____ command.
a. Layer, Distribute, Top Edges b. Layer, Distribute, Vertical Centers c. Layer, Distribute, Bottom Edges d. Layer, Distribute, Left Edges
When you don't know the specific value to include in the criteria, you use a ____.
A. limited query B. tagged query C. structured query D. parameter query
Which video mode is used in 24"+ widescreen monitors?
A. XGA B. UXGA C. SXGA D. WUXGA