Which of the following physical security methods provides the ability to secure a company's assets and document any individuals physical time of entry?
A. rotary locks
B. combination locks
C. card access
D. deadbolt locks
Answer: C
Computer Science & Information Technology
You might also like to view...
If your document has no heading styles, PowerPoint will create slides based on ________ only
Fill in the blank(s) with correct word
Computer Science & Information Technology
Referring to the figure below, please identify the letter of the choice that best matches the numbered area on the screen.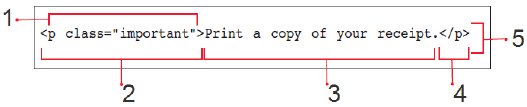
A. Attribute B. Opening tag C. Content D. Closing tag E. Element
Computer Science & Information Technology
To create a nested frameset, you will use a ____ tag inside another of the same tag to create both vertical and horizontal frames.
A. B.
Computer Science & Information Technology
The ____ is the most important part of testimony at a trial.
A. cross-examination B. direct examination C. rebuttal D. motions in limine
Computer Science & Information Technology