?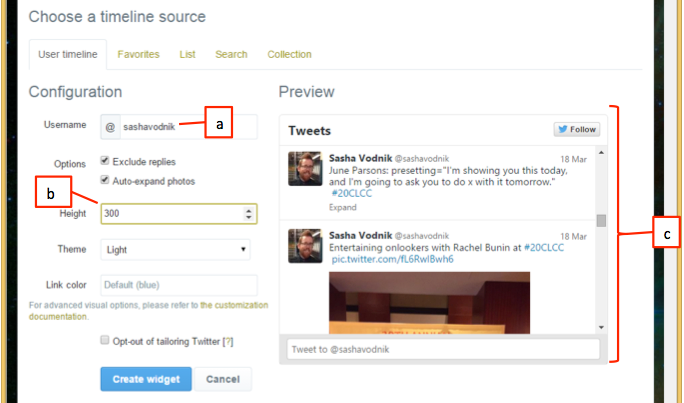
?
Referring to the figure above, which item indicates the hash tag to use as the source for the widget?
A. a
B. b
C. c
D. none of these
Answer: D
You might also like to view...
This stands for Wi-Fi Protected Access, and it supports the user authentication provided by 802.1x and replaces WEP as the primary way for securing wireless transfers.
What will be an ideal response?
Compute the area of half of a 3-inch by 6-inch rectangle cut along its diagonal.
What will be an ideal response?
A deliberate politically or religiously motivated attack against data compilations, computer programs, and/or information systems which is intended to disrupt and/or deny service or acquire information which disrupts the social, physical, or political infrastructure of a target is known as cyberterrorism
Indicate whether the statement is true or false.
If a primary DNS server goes down, the secondary servers can resolve FQDNs and add new records.
Answer the following statement true (T) or false (F)