____________________ is the process by which the information technology and information security teams position their organizations to prepare for, detect, react to, and recover from man-made or natural events that threaten the security of information resources and assets.
Fill in the blank(s) with the appropriate word(s).
CP
You might also like to view...
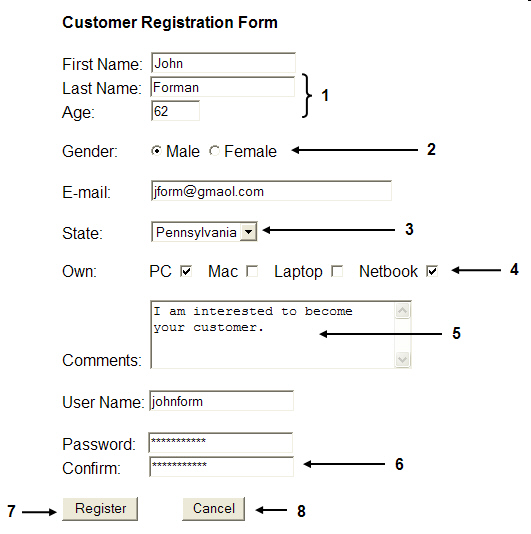 The ____ attribute for the item marked 7 in the accompanying figure is Register.
The ____ attribute for the item marked 7 in the accompanying figure is Register.
A. selection B. option C. value D. key
Match the following dialog boxes to their features or options:
I. Microsoft Office Security Options dialog box II. Record Macro dialog box III. Trust Center dialog box IV. Visual Basic editor V. Properties dialog box A. name a macro B. edit a macro C. select date formats in Date Picker D. enable macro content E. change macro security settings
Under the Federal Rules of Civil Procedure, which two rules regulate the production of evidence?
A) Rules 34 and 23 B) Rules 26 and 35 C) Rules 25 and 33 D) Rules 26 and 34
When you move interactive button images into a new folder, Expression Web prompts you to update the links manually.
Answer the following statement true (T) or false (F)