Information security work involves a very wide range of ____.
A. required activities
B. required competencies
C. potential activities
D. potential competencies
Answer: C
You might also like to view...
Answer the following statement(s) true (T) or false (F)
1. ICONs and OCONs can be used to exchange information between instructions. 2. A function block routine can be broken into multiple sheets. 3. Additional sheets in a function block routine are executed when called by a JSS instruction. 4. When a function block routine executes, only the currently selected sheet executes. 5. Only one FB routine may be used per project.
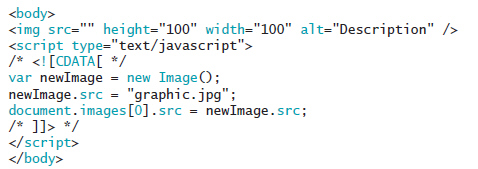 What is the purpose of the code seen in the accompanying figure?
What is the purpose of the code seen in the accompanying figure?
A. animation B. changing an image directly C. caching and then changing an image D. displaying the same image
What is the term for an electronic document on the web that can contain text, graphics, animation, audio (sound), and video?
A. webpage B. webnet C. web reader D. web host
The background area behind and to the left of a chart's bars is called the ____.
A. background wall B. chart wall C. chart background D. chart variation