An administrator is securing a secure web server by disabling ports. After completing this process, clients cannot access the secure web server. The administrator should now go back and verify whether which of the following ports is enabled?
A. 23
B. 389
C. 443
D. 445
Answer: C. 443
You might also like to view...
Discuss how you would test for view serializability using a labeled precedence graph. Using the above method, determine whether the following schedules are view serializable:
(i) S 1 = [R 1 (x), W 2 (x), W 1 (x)]
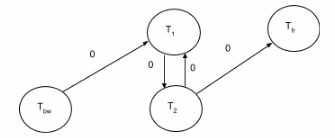
(ii) S 2 = [W 1 (x), R 2 (x), W 3 (x), W 2 (x)]
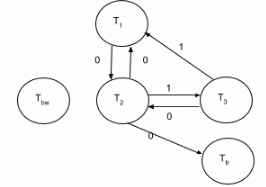
(iii) S3 = [W1(x), R2(x), R3(x), W3(x), W4(x), W2(x)]
The ____ can be used to determine whether two stacks are identical.
A. rational operator B. logical operator C. relational operator D. arithmetic operator
?A _________ is a border that is based on a graphic image.
Fill in the blank(s) with the appropriate word(s).
Identified as a critical strong point in the network’s security, the _________ serves as a platform for an application-level or circuit-level gateway.
Fill in the blank(s) with the appropriate word(s).