To make a check box selected by default, you add ____.
A. selected="true"
B. selected="selected"
C. checked="checked"
D. checked="true"
Answer: C
You might also like to view...
Several techniques have been proposed for the distribution of public keys. The proposals can be grouped into the following four general schemes: public announcement, publicly available directory, public-key certificates, and ____________.
Fill in the blank(s) with the appropriate word(s).
Answer the following statement(s) true (T) or false (F)
1. Custom frameworks are easy to design but difficult to implement. 2. A threat is a weakness in the asset. 3. In the FAIR framework, the risk score is calculated based on the impact and likelihood. 4. Likelihood is the probability that an asset is attacked with a negative impact. 5. An asset is always a direct target of a threat.
?You are being consulted for recommendation on software for sales report management. There are two choices. Choice #1 is a product from an industry leader that costs more than $1,000 per license per year. The second choice is a free open-source software that is free to download and install. The free software is in a language that your programmers do not have expertise in. You may be able to convince management to hire the right programmer to install the free and open source software. Considering the importance of data security, what solution would you recommend, and why?
What will be an ideal response?
Find the area of the shaded parts of the following figure. Round your answer to the nearest hundredth.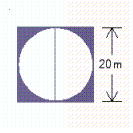 __________
__________ ![]()
Fill in the blank(s) with the appropriate word(s).