Does parallel processing in the form of multicore processors represent the future … or the past?
What will be an ideal response?
Parallel computing has a long history and has been used to create supercomputers for a long time. It could be argued that the move to high?performance computing using commodity devices like the IA32 architecture rather than arrays of powerful processors was quite a conservative step. In some ways, you could think of multicore processors as a blast from the past (i.e., a tried?and?tested technique that has caught up with modern technology).
However, the development of the multicore processor and the highly parallel GPU processors has had a considerable impact on the development of parallel processing and the tight coupling of processors (including common cache systems). Consequently, it is a thing of the future. However, it may be a thing of the near future only, if new developments in computer architecture and organization lead to other ways of computing and multicore processing falls out of fashion.
You might also like to view...
The default rotation is ____.
A. From Left B. From Right C. From Top D. From Bottom
The ____________________ oversees development of an entire project, including storyboard and development timeline.
Fill in the blank(s) with the appropriate word(s).
FIGURE 13-2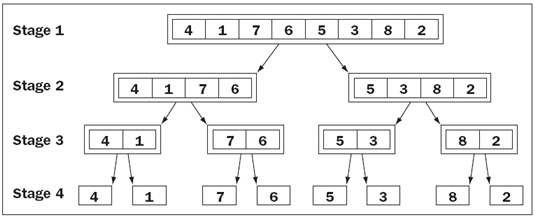 Figure 13-2 above shows subarrays generated during calls of ____.
Figure 13-2 above shows subarrays generated during calls of ____.
A. quickSort B. binarySort C. mergeSort D. bubbleSort
In Open System Authentication, how does authentication occur?
a. The client sends a pre-shared key along with the access point's SSID. b. The client requests an encrypted tunnel, after which, the client's MAC serves as the authentication. c. The access point forces the client to authenticate via a captive portal, after which all communication is encrypted. d. The client "authenticates" using only the SSID name. In other words, no real authentication occurs.