?Some businesses outsource their security management to MSSPs. MSSP stands for ________.
Fill in the blank(s) with the appropriate word(s).
managed security service provider
Computer Science & Information Technology
You might also like to view...
Write the line of code that would define a variable called prices, which is of template class indexList, containing at most 50 prices of items.
What will be an ideal response?
Computer Science & Information Technology
____ attacks exploit the existing software weaknesses. The effect is either degraded performance or crashes on the victim server.?
A. ?Software B. ?Flood C. ?Voluntary D. ?Isolated
Computer Science & Information Technology
____ Drawing mode assumes that the objects' path will combine in some fashion.
A. Object B. Merge C. Stroke D. Resolved
Computer Science & Information Technology
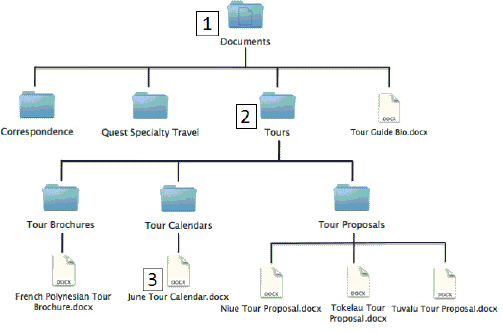 In the accompanying figure, Item 1 represents a ____.
In the accompanying figure, Item 1 represents a ____.
A. Subfolder B. Toolbar C. Folder D. File
Computer Science & Information Technology