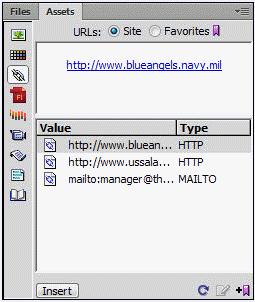
In the figure above, the three links in the Assets panel are ____ links.
A. related pages
B. internal
C. ?external
D. ?relative path
Answer: C
You might also like to view...
Given the following array declaration, what value is stored in testScores[2][0]?
``` Declare Integer testScores[3][3] = 66, 77, 88, 98, 87, 76, 65, 74, 89 ``` a. 98 b. 88 c. 89 d. 65
Answer the following statements true (T) or false (F)
1. A widely used technique for pseudorandom number generation is an algorithm known as the linear congruential method. 2. A cryptographically secure pseudorandom bit generator is defined as one that passes the least significant bit test. 3. The security of Blum, Blum, Shub is based on the difficulty of factoring n. 4. The stream cipher is similar to the one-time pad with a difference being that a one-time pad uses a pseudorandom number stream and a stream cipher uses a genuine random number stream. 5. The longer the keyword the more difficult the cryptanalysis.
The ________ date format is applied to the date Tuesday, January 31, 2012
Fill in the blank(s) with correct word
The ____ statement provides an unconditional transfer of control to some other statement in a program.
A. jump B. goto C. label D. transfer