Using the ________ gives you access to the most common formatting selections, such as adding bold or italic, or changing font type or color.
Fill in the blank(s) with the appropriate word(s).
mini toolbar
You might also like to view...
Consider the data set shown in Table 7.8. The first attribute is continuous, while the remaining two attributes are asymmetric binary. A rule is consid- ered to be strong if its support exceeds 15% and its confidence exceeds 60%. The data given in Table 7.8 supports the following two strong rules:
(i) {(1 ? A ? 2), B = 1}?{C = 1}
(ii) {(5 ? A ? 8), B = 1}?{C = 1}
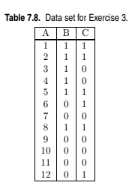
(a) Compute the support and confidence for both rules(b) To find the rules using the traditional Apriori algorithm, we need to
discretize the continuous attribute A. Suppose we apply the equal width
binning approach to discretize the data, with bin-width = 2, 3, 4. For
each bin-width, state whether the above two rules are discovered by
the Apriori algorithm. (Note that the rules may not be in the same
exact form as before because it may contain wider or narrower intervals
for A.) For each rule that corresponds to one of the above two rules,
compute its support and confidence.
(c) Comment on the effectiveness of using the equal width approach for
classifying the above data set. Is there a bin-width that allows you to find both rules satisfactorily? If not, what alternative approach can you
take to ensure that you will find both rules?
The recursive definition of a Fibonacci Number is F(n) = F(n-1) + F(n-2), where F(0)=1 and F(1)=1. What would be the recursive function call in a recursive implementation of this?
a. return; b. return fib(n) + fib(n-1) c. return fib(n-1)+fib(n-2) d. return 1;
You cannot enable your computer to act as a Remote Desktop Connection host if you have which one of the following Vista editions?
A) Vista Ultimate B) Vista Home Basic C) Vista Business D) Vista Enterprise
Suppose processes P1, P2 and P3 have time stamps 1, 2 and 3, respectively. If P3 requests a resource held by P2, which process will be rolled back using the wait-die algorithm?
What will be an ideal response?