To achieve an effective ____ focus, the governance process should document the requisite day-to-day actions of the everyday information security function down to whatever level of detail is necessary to ensure consistent performance.
A. tactical
B. strategic
C. operational
D. practical
Answer: C
Computer Science & Information Technology
You might also like to view...
In a secret key system
a. some keys are secret and some keys are public b. keys must originally be sent over a secure channel c. keys may never be changed d. keys are chosen by an administrator
Computer Science & Information Technology
What security issues are liable to be relevant to a directory service such as X500 operating within an organization such as a university?
What will be an ideal response?
Computer Science & Information Technology
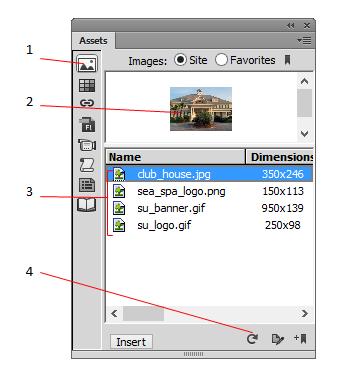
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
To check out a file in Dreamweaver, you should click the file you want to work on in the ____ panel, then click the Check Out File(s) button on the Files panel toolbar.
A. Assets B. Layers C. Site D. Files
Computer Science & Information Technology