Experiment with the hidden-form example presesnted in Figures 21a through 21c.
a. Obtain the source files for form.html, hidenForm.c, hiddenForm2.c.
b. Install form.html on the web server.
c. Compile hiddenForm.c with util.c to generate an executable hiddenForm.cgi. Install hiddenForm.cgi on the web server.
d. Compile hiddenForm2.c with util.c to generate an executable hiddenForm2.cgi. Install hiddenForm.cgi on the web server.
e. Browse form.html. Does the session data (the name entered in the static form) get passed to the last web script?
f. Summarize the experiment and your observations.
e. Yes. See below.
The screen captures are presented below:
The initial page:
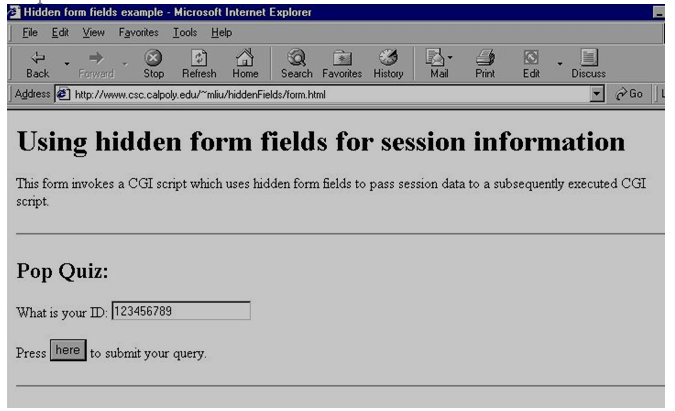
When the page is submitted, hiddenForm.cgi is executed by the server, and the web page that it generated is received by the browser and displayed as follows:
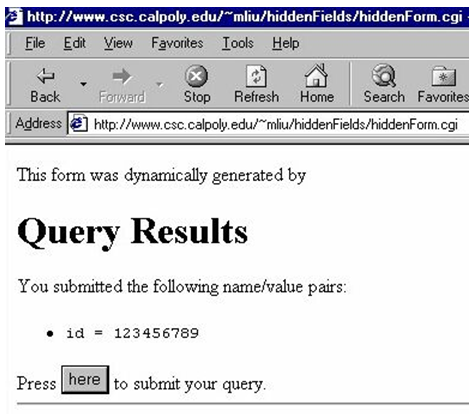
The source code of the page above, generated by hiddenForm.cgi:
```