Match each item with a statement below.
A. Procedures based on a mathematical formula used to encrypt and decrypt the data
B. Cryptography that uses two mathematically related keys
C. The unique digital fingerprint created by a one-way hash algorithm
D. A mathematical value entered into a cryptographic algorithm to produce encrypted data
E. Unencrypted data
F. The process of proving that a user performed an action
G. An asymmetric encryption key that must be protected
H. An asymmetric encryption key that does not have to be protected
I. Encryption that uses a single key to encrypt and decrypt a message
A. algorithm
B. asymmetric cryptography
C. digest
D. key
E. cleartext
F. nonrepudiation
G. private key
H. public key
I. symmetric cryptography
You might also like to view...
What technologies help make printed or displayed text accessible to people who are blind?
What will be an ideal response?
What will be output from the following code:
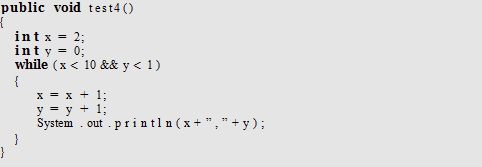
A check digit is a digit that is added in the middle of a number to validate the number's authenticity.
Answer the following statement true (T) or false (F)
If there is an element of a layer that you wish to protect, such as transparency, you can ____________________ it to prevent changes.
Fill in the blank(s) with the appropriate word(s).