Find the x- and y-intercepts of the equation and use them to sketch the graph. 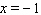
A. 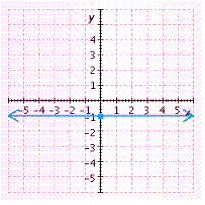
x-intercept none , y-intercept ![]()
B. 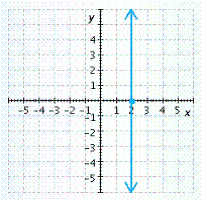
x-intercept ![]() , y-intercept none
, y-intercept none
C. 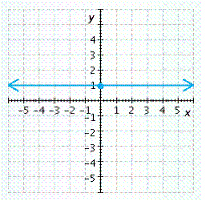
x-intercept none , y-intercept ![]()
D. 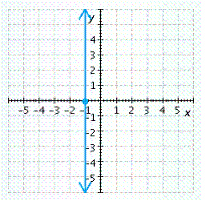
x-intercept ![]() , y-intercept none
, y-intercept none
E. 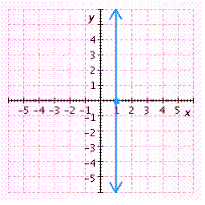
x-intercept ![]() , y-intercept none
, y-intercept none
Answer: D
You might also like to view...
Which PHP function returns the timestamp of the time the file was last modified?
a. file m time() b. file a time() c. file type() d. file perms()
Cover pages are numbered, but the page number is ____.
A. suppressed B. formatted in bold C. grayed out D. none of these
Match the protocol or encryption name with the feature.
A. No longer considered secure because the key used for encryption doesn’t change. B. Typically uses TKIP for encryption. C. Typically uses AES for encryption. D. Generates a different key for every transmission; however, the encryption algorithm used for its calculations is no longer considered secure. E. Current encryption algorithm used today.
What are the tasks you must perform when you declare a class that handles an event?
What will be an ideal response?