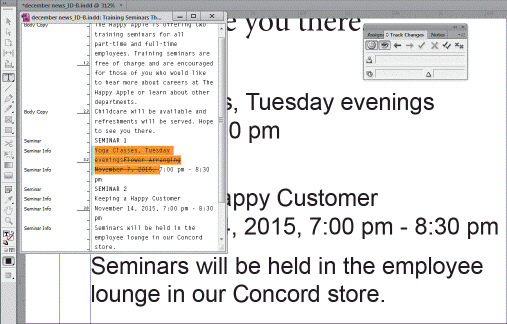
 As shown in the accompanying figure, text that is marked for ____________________ has the strike through applied to it.
As shown in the accompanying figure, text that is marked for ____________________ has the strike through applied to it.
Fill in the blank(s) with the appropriate word(s).
deletion
Computer Science & Information Technology
You might also like to view...
These are the basic form of firewall protection.
What will be an ideal response?
Computer Science & Information Technology
A person searches for wireless networks from his car. What is this an example of?
A. Wardriving B. DDoS C. Replay attack D. Bluejacking
Computer Science & Information Technology
While many are pushing wireless networking, in reality wireless networks have several disadvantages when compared with 100BaseT and Gigabit Ethernet. Name at least two disadvantages of wireless networks.
What will be an ideal response?
Computer Science & Information Technology
Once text has been flowed into an object, you can still manipulate the fonts and font size of the object.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology