Give an example execution of the ring-based algorithm to show that processes are not necessarily granted entry to the critical section in happened-before order.
What will be an ideal response?
Consider three processes in a ring, in the order P1, P2 and P3. Note that processes may send messages to one another independently of the token-passing protocol.
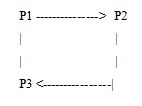
The token is initially with P2. P1 requests the token, then sends a message to P3, which also requests the token. The message passes the token at P2. Then P2 sends on the token. P3 gets it, but the token should have been granted to P1 first.
You might also like to view...
List three recommendations to help secure a wireless network.
What will be an ideal response?
Which of the following could become a member of the Internet2?
A) CNN B) Amazon C) Facebook D) Library of Congress
When creating an index, you must identify the ________ that will be used as index entries
A) bookmarks B) page numbers C) terms D) formats
The philosophy behind the ____ model is that we use a network to share resources that are too widespread, too expensive, or used too infrequently to warrant replication at every node.
broadband client/server integrated virtual